Information Security Risk Management
Information Communication Security Management Strategy and Framework
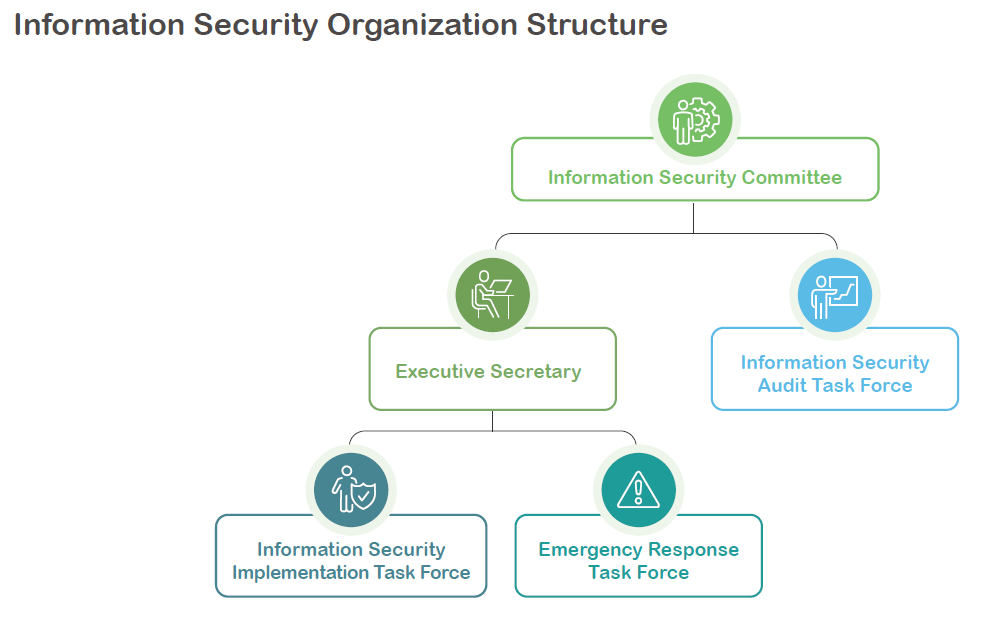
In 2021, Nan Pao established the "Information Security Committee," responsible for executing information operation security management planning, establishing and maintaining an information security management system, coordinating the formulation and implementation of information security and protection policies, as well as conducting risk management and compliance audits. The Information Security Committee is chaired by the CEO, with Mr. Guo Peiyi, the Associate Manager of the Information Department, serving as the Chief Information Security Officer and Executive Secretary. The committee includes senior executives from various functional units.
Additionally, we have established the "Information Security Audit Team" and the "Information Security Execution Team," responsible for planning and auditing information security and physical security matters within the company. These teams play a leading role in the operation of the committee.
l The Information Security Management Committee is responsible for establishing information security management policies and procedures, with regular reviews and revisions.
l The Information Security Management Committee holds periodic review meetings to ensure the smooth operation of management mechanisms and reports to the Board of Directors annually.
l The IT Department includes an Information Security Officer, cybersecurity managers, and personnel, who coordinate all cybersecurity-related policies, implementation, and the planning and establishment of the cybersecurity defense framework.
Information Security Policy
The Company’s Information Security Policy applies to the Company and its domestic and overseas subsidiaries, and is guided by the following principles:
l Strengthen information security management to ensure the confidentiality, integrity, and availability of information assets.
l Provide an information environment that supports the continuous operation of the Company’s information-related business.
l Comply with relevant laws and regulations to protect against intentional or accidental internal and external threats.
The Company has implemented and established a comprehensive Information Security Management System (ISMS). It obtained ISO 27001:2013 certification in 2022 and successfully transitioned to ISO 27001:2022 in 2025. The current certificate is valid from July 22, 2025, to July 22, 2028.
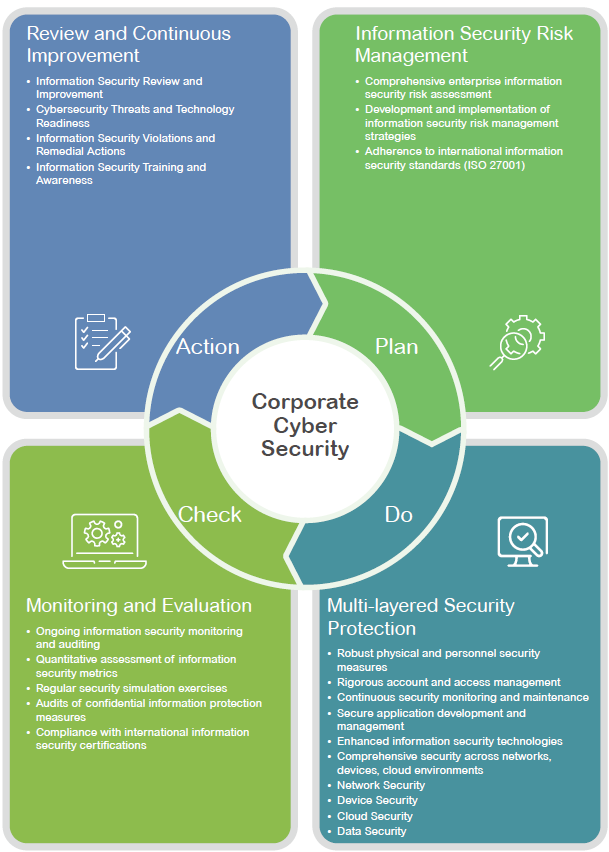
The system mitigates cybersecurity threats from system, technical, and procedural perspectives, creating an information security environment that meets customer requirements. The Company continuously applies the Plan-Do-Check-Act (PDCA) management cycle to ensure ongoing improvement in information security.

Specific Management Measures
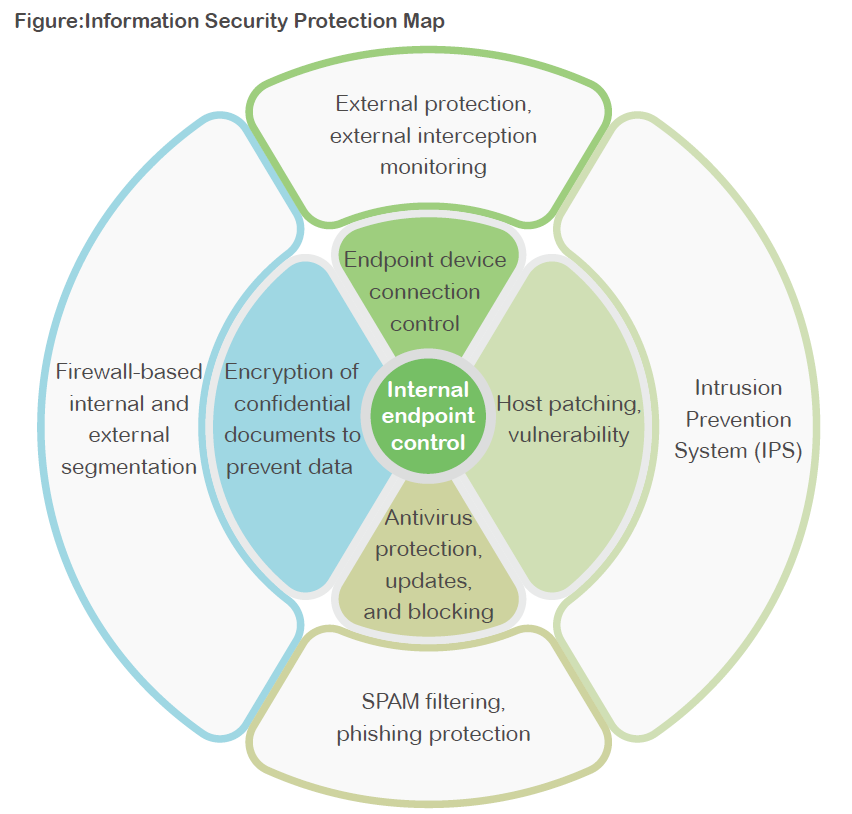
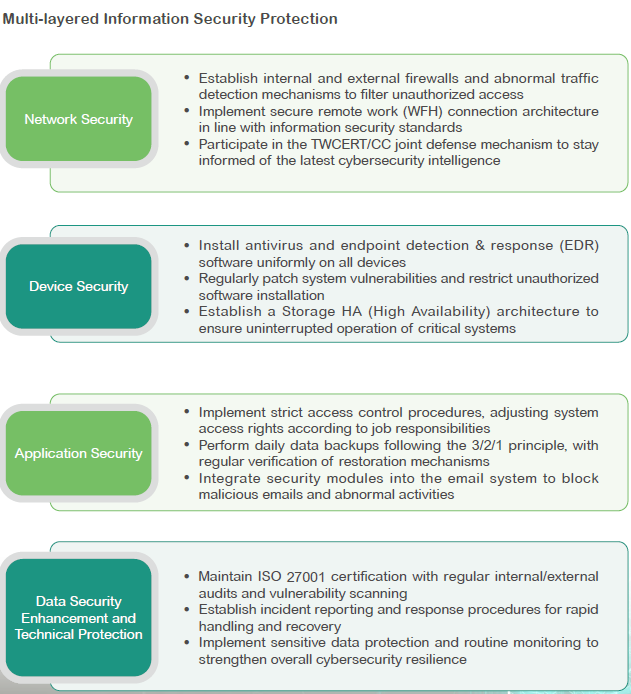
To achieve its information security policies and objectives, the Company has established an “Information Security Protection Map” and implements proactive security enhancement measures. Key mechanisms include:
l Deployment of next-generation firewalls and intrusion prevention systems (IPS)
l Malware and spam email filtering
l Regular operating system updates and antivirus software deployment
l Encryption of confidential documents and endpoint connection controls
l Establishment of network segmentation, isolating networks according to their specific purposes
l Regular patching of operating systems and application vulnerabilities
l Implementation of off-site backups for critical data and documents
These measures collectively create layered defenses and ensure that, in the event of external network attacks, the risk of widespread internal damage is minimized.
Through its internal risk management mechanisms, the Company assesses risks related to information systems and regularly reports the status of risk controls and improvement measures at management meetings in order to control and mitigate cybersecurity risks.
Each year, the Company conducts information security training programs to enhance employees’ awareness of information security. In addition, information security policies and knowledge are regularly communicated via email, and topic-specific seminars are held periodically during weekly meetings to reduce the risk of employees clicking on malicious emails. The Company also regularly updates and patches operating systems and application vulnerabilities, and implements off-site backups for critical data and documents.

Resources Invested in Information and Cybersecurity Management
² Information Security Certification:
- Successfully obtained ISO 27001:2022 information security certification in June 2025.
- The subsidiary Nan Pao Vietnam continued to obtain the ISO 27001:2022 surveillance certification in 2025.
² Education and Training:
- In 2025, all 48 newly hired employees at headquarters completed a 1-hour pre-employment information security training course.
- The information security officer and cybersecurity personnel obtained certificates of completion for the “2024 Cybersecurity Training Program for Listed (OTC) Companies” on December 21, 2024, and February 27, 2025, respectively. They are also scheduled to complete the “2025 Cybersecurity Training Program for Listed (OTC) Companies” organized by the Taiwan Stock Exchange by May 31, 2026.
² Information Security Awareness Promotion:
- In 2025, two information security policy and regulation announcements were distributed monthly via email, along with periodic sharing of recent cybersecurity incident cases for reference.
- A “Cybersecurity Awareness” seminar was held during the weekly meeting on March 12, 2025, communicating key cybersecurity protection requirements and precautions. A total of 356 attendances participated, with a cumulative duration of 89 hours.
- A social engineering phishing email simulation was conducted once by the end of December 2025, involving 500 participants.
² Customer Satisfaction:
- In 2025, there were no customer complaints related to data breaches or loss of customer information.
n The Company convened the Information Security Committee on December 10, 2025, and reported to the Board of Directors on December 18, 2025, regarding the establishment and implementation status of the 2025 Information Security Risk Management Framework.
|
Information security incident management |
2025 |
|
Total number of information security incidents |
0 |
|
Number of information security incidents affecting customers’ personal information |
0 |
|
Total number of customers affected by information security incidents |
0 |
|
Total amount of fines related to information security incidents |
0 |
